Remote monitoring powered by cloud services
Machines, equipment skids and automation systems used for manufacturing and processing facilities are more connected than ever. Some of the newest equipment may come with cloud-capable controllers, but many users are adding gateways or other devices to make the connection from legacy operations technology (OT) systems to information technology (IT) logging, visualization and computing resources.
Cloud networks are often the best way to interconnect and manage many data sources for an industrial internet of things (IIoT) implementation, but only if users understand the potential data security risks and take the right steps to address them.
Creating this type of a solution from scratch is a complex undertaking and may not be secure. Fortunately, there are complete solutions available that are tailored to the needs of industrial users who need to connect OT data quickly and easily to IT resources.
This article describes why cloud-capable routers and an associated cloud solution — designed using a comprehensive information security management system (ISMS) — are often the best all-in-one solution for safely and easily setting up remote access, remote monitoring and alert functionality.
Security, bottom to top
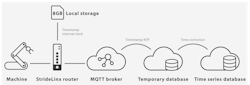
Industrial remote connectivity and monitoring solutions include hardware and software elements on-premises at the production facility and in the cloud, as well as all the networking functionality in between. A typical solution uses a site-located intelligent router to provide secure remote access with local machines and has the capability to log and then transmit machine or process data to cloud servers over the internet (Figure 1).
As the following sections will describe, it is a significant endeavor to create a safe, reliable and trustworthy IIoT solution of this type. Therefore, choosing an off-the-shelf solution providing routers and cloud services is typically the best way to ensure all elements are optimal. To start, the solution should be certified according to the ISO 27001, which addresses information security management, and should provide the following capabilities and functionalities.
Router security
Most legacy controllers used for processes, equipment and facilities were never designed for security — and even the few that were, are rarely updated. Therefore, these controllers should never be connected to a company network or the internet directly. Instead, they should reside on a plant network, which in turn, must be isolated from the internet using a router with a built-in firewall.
By default, the router firewall should block all traffic between the machine local area network (LAN) and the company/cloud wide area network (WAN) (Figure 2). Of course, to configure remote connectivity on standard routers requires significant understanding of communications and IT networking. This can be a complex task to perform manually, requiring skilled personnel to create and manage these settings.
For this reason, a router that automatically connects to a secure comprehensive cloud-based solution is a better approach. The cloud solution should also provide a health indication of all associated routers, as well as notifications if a router goes offline for any reason.
There are a few more characteristics needed to ensure cloud-capable routers are securely implemented:
- Secure connectivity protocols: HTTPS, MQTT over TLS, and secure virtual private network (VPN) connectivity are three of the most popular protocols to establish and maintain secure and encrypted cloud communications for remote monitoring and connections.
- Only outgoing ports: Because most IT groups will block incoming internet communications, it is essential for routers to establish secure connections using only outgoing ports, which will be sufficient for most sites.
- Access restrictions: Industrial routers must work well with site IT security standards, while addressing the needs of OT users. This means the router should be capable of using a static or automatic DHCP IP address, and it should also accept a hardwired digital input to enable or lockout remote access.
- Two-factor authentication: Solutions should include the capability to mandate two-factor authentication as part of the user management system, as an additional security step to strengthen the account by requiring users to verify their identity using a one-time password method.
- Router failover: Site network connections are not always stable, so an industrial router must be capable of using a primary/preferred network and then performing a failover to a secondary/fallback network as needed. This functionality should be available for Wi-Fi, 4G and Ethernet networks.
- Local data logging: For the same reason router failover is important, the router must also include significant on-board memory to log data offline while a connection is not available and then transmit the data when the router is back online.
Cloud security
Some users might consider creating their own cloud server configurations. However, there are many issues that make this type of system complex to develop from scratch. As with the routers, a better choice is to use a commercially available cloud services solution structured for the best availability and security, as well as required performance.
Cloud services providers offer a network of dozens of servers, distributed in ISO 27001 certified data centers located worldwide (Figure 3). Some servers are necessary for data handling roles, while others support VPN connections. The VPN server network is typically distributed across the globe to provide low latency connections, along with redundancy so if one server goes down, the others will take over automatically. This is particularly important because VPN connectivity supports HMI and web-based visualization.
Cloud server implementations should also address each of the following aspects:
- Data ownership: Users should ensure the cloud services provider confirms that all data is owned by the users and not by the service provider.
- Kubernetes cluster: This open-source technology is a high-performance way of deploying, scaling, and managing applications, which makes it an ideal platform for offering cloud services.
- Relational database: A redundantly configured relational database cluster is necessary to store information about cloud server devices and users.
- Non-relational database: Events such as alarms and logs should be stored in a non-relational database cluster to optimize required storage resources, and it should be replicated for high availability.
- Time-series database: Process and operational data consists of timestamped values delivered via MQTT, so they require a specific time-series database cluster optimized for quickly accessing and performing computations on large data quantities in an efficient manner.
- Browser and app security: Because the cloud platform is accessed via browsers and apps, there needs to be a way of managing and authenticating administrators and users.
- VPN tunnels: The cloud service should also enable secure VPN tunnel connections in a way such that third-party apps can securely access the cloud data. This provides the best end user flexibility to use apps of their choosing.
- Management services: Cloud computing solutions should include centralized monitoring, logging, and analytics to detect anomalies in a timely manner. An independent third-party should periodically scan the cloud services for vulnerabilities and audit the servers. Access control policies should carefully limit which developers can work on servers and software, and software changes should be reviewed by at least one other developer prior to deployment, with a versioning system used to provide backups.
Remote monitoring performance and security
Most processing companies would like to take advantage of remote monitoring, access and visualization of their automated systems. But for many, it would be difficult to create a comprehensive solution from scratch, especially one that performs under adverse conditions and follows ISO security standards. Even if such a solution could be created in-house, maintenance and upgrades would be very challenging and resource intensive.
By choosing an end-to-end solution with cloud-capable routers and an associated cloud solution developed using the latest standards and technologies, these users can quickly implement a safe, reliable and trustworthy IIoT platform.
Jonathan Griffith is the product manager for Industrial Communications & Power Supplies at AutomationDirect. Prior to joining AutomationDirect in 2015, he worked at ANADIGICS from 2002 to 2014, a Wi-Fi networking company. Griffith holds three degrees, all from the Georgia Institute of Technology: an MBA, an MSEE and a BSEE.
AutomationDirect
About the Author
Jonathan Griffith
Jonathan Griffith is the product manager for Industrial Communications & Power Supplies at AutomationDirect. Prior to joining AutomationDirect in 2015, he worked at ANADIGICS from 2002 to 2014, a Wi-Fi networking company. Griffith holds three degrees, all from the Georgia Institute of Technology: an MBA, an MSEE and a BSEE.