Minimizing cybersecurity risks with preventive maintenance
Recent technological advances and a shift to remote maintenance due to the COVID-19 pandemic has spurred the widespread adoption of the Industrial Internet of Things (IIoT). IIoT is the concept of interconnecting assets to condition monitoring sensors and software, thus permitting integration with PCs and mobile devices.
IIoT allows for innovative maintenance and reliability solutions, from supervisory control and data acquisition (SCADA) systems to real-time condition monitoring of programmable logic controllers (PLCs). But connecting a manufacturing plant to the internet also greatly increases the risk of cyberattacks.
More than 100 manufacturing professionals rated the importance of cybersecurity when considering maintenance and reliability software solutions in a recent Fluke Reliability survey. Of the respondents, 68% said cybersecurity was “Mission Critical,” while 32% said it was “Somewhat Important.” Zero respondents listed cybersecurity as “Not Important” or “Not Sure.”
Without hardened software systems, a cyberattack might be inevitable. But the above evidence indicates manufacturing facilities are taking the threat of cyberattacks seriously, and recent advancements have made it possible to greatly improve the strength of IIoT systems against cyberattacks.
How Cyberattacks Impact the Manufacturing Industry
Ransomware attacks on well-known companies have dramatically increased over the years. And cybercriminals consider the manufacturing industry to be a high-value target.
According to a June 2021 research report from Morphisec, 20% of manufacturing companies in the U.S. and U.K. had been victims of cyberattacks in the last 12 months. And nearly 25% of all ransomware attacks are carried out on manufacturing companies.
Phishing, data theft, supply chain and ransomware attacks should now be expected. Typically, malicious actors steal credentials, expose sensitive data and hold intellectual property ransom. Some cyberattacks are so damaging they force companies to pause or entirely halt operations, costing millions of dollars in downtime.
One such example involves the Russian criminal group REvil, which stole confidential files from Apple partner Quanta Computer Inc., the world’s largest laptop manufacturer. The REvil hackers attempted to extort $50 million from Quanta in exchange for the return of stolen schematics and images related to an upcoming laptop release.
It is unknown whether Quanta paid that ransom, but another company, JBS USA Holdings Inc, acknowledged paying the same Russian criminal group an $11 million ransom to prevent further disruption following a hack that forced JBS to completely shut down its plants.
Defending Against Cyberattacks with Preventive Maintenance
Scheduling preventive maintenance (PM) tasks is vital to keeping equipment operating. But it is not the only kind of necessary maintenance. Performing regular preventive maintenance on SCADA, PLC and Computerized Maintenance Management Systems (CMMS) also helps reduce cybersecurity vulnerability.
Hardening is a form of cyberattack protection that involves eliminating system gaps that hackers often utilize to seize control of a system and gain access to sensitive data. To keep a cybersecurity environment hardened, it is important to schedule downtime to allow for software updates and system patches. It is also critical to develop a plan, including response protocols and disaster recovery plans, for when an attack occurs.
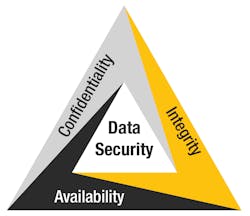
Improving Cybersecurity with the CIA Triad
Confidentiality, integrity and availability are the three pillars of what is known as the CIA triad. If one or more of these components is violated, the risk of an attack increases. Organizations often build their cybersecurity foundations around this three-pronged model.
Establishing information security policies based on the CIA triad helps organizations make essential decisions about which cybersecurity components are most applicable to protecting specific data sets, such as sensor data.
Best Practices for Deploying the Cybersecurity Triad
Maintaining data confidentiality is necessary to ensuring that private information is only accessible to vetted individuals. Only core personnel should have permission to access data. To reduce the possibility of a cybersecurity breach, limit entry points to sensitive data to as few people as possible. Scrutinize who has access and only grant permissions to those who need the data to do their jobs.
An organization should also examine its data access levels, including for sensitive data that permits control over essential equipment, such as a SCADA system. Many organizations categorize the importance of data by how much damage would result from its unauthorized release.
It is important to note that the human element is one of the primary causes of company data breaches, so a regularly educated workforce is one of the strongest possible defenses against potentially damaging cybersecurity threats.
Ensuring data integrity is another cybersecurity best practice, as it is important to know that data is trustworthy, accurate and unaltered. Data integrity refers to the validity and accuracy of the data throughout its lifecycle. A company’s operations department, as well as its ability to demonstrate regulatory compliance, depends on reliable data.
Inaccurate data can lead to damaged relationships with customers, costing companies lots of money. According to a 2013 Gartner study, organizations surveyed estimated that inaccurate data costs them an average of $14.2 million annually. That importance has only increased since in the years since then.
An organization should evaluate their level of data accuracy in their primary systems, performing a full audit if the data seems untrustworthy. Determine a required level of confidence for maintenance records and identify vulnerability points, further protecting them if necessary. Adopt controls that prevent unauthorized users from making erroneous changes or accidently deleting data.
Maintaining data availability is vital to ensuring that data is readily accessible to those who require it to make timely, data-driven decisions. The on-demand data should include uptime percentage, which enables an enterprise asset management (EAM) system and other critical systems to continuously supply what is needed.
Maintenance systems also must be protected from corruption. An organization should carry out preventive maintenance (PM) best practices on the IT infrastructure supporting their processes. It is necessary to understand what is required to maintain data availability, and to consider the optimal timing for scheduling downtime to deploy patches that harden the system, thereby reducing external entry points.
Protecting the confidentiality, integrity and availability of sensitive data is key to the implementation of a successful cybersecurity plan. To do this, operations, maintenance, and IT teams must work together closely to efficiently and effectively mitigate cybersecurity issues by developing high-level IIot and cybersecurity checklists that include things like equipment, communications, protocols, environment and security concerns.