Cybersecurity must be at the heart of the evolving connected automation platform
There are two unfortunate circumstances in today’s operational technology (OT) cybersecurity landscape. The first is that the percentage of non-cybersecure OT installations — including those running on legacy or unsupported hardware and software — is still very high. The second is that cyber threats continue to increase daily, both in number and severity, and are more frequently targeting process manufacturers, with the intent to disrupt supply chains. Various contributing factors create these problems: tight resources, limited experienced personnel, lack of corporate direction and more.
For years, those concerns have led OT to take a different approach to its technology than other groups, isolating the control system to help ensure its reliable, safe and secure operation. But today that isolationist approach is hindering innovation, flexibility and performance across the enterprise. Old technologies with no ability to securely connect to the cloud limit visibility and competitive advantage, but the paradigm is changing.
Industrial plants are modernizing their technologies with secure-by-design automation platforms built with enterprise connectivity in mind. These systems provide better overall cybersecurity, while simultaneously unlocking the capabilities needed to drive a more efficient and sustainable future of automation.
Why today?
Many plants running control systems that are 20, 30 or even 40 years old are discovering that the original vendors no longer offer support for those products. And in the rare case where a vendor does still support those systems, the services they provide for old technologies and obsolete systems are typically limited, leading to long wait times and high costs. Moreover, plants are identifying high opportunity costs associated with running old automation technology. Many of today’s best practices — including critical cybersecurity components — simply do not work well, if at all, with those older systems.
Process manufacturers are also striving to meet new needs in the marketplace, including increased throughput and more sustainable operations. These needs are in turn driving a new requirement for edge connectivity to the cloud for driving enterprise analytics and other advancements. This increasing use of, along with access to, the cloud further underscores the need for modern, effective cybersecurity.
Conundrum at the convergence
For well over a decade, information technology (IT) groups have assumed connectivity as a given. They have been focused for years on secure methods for ensuring systems have access outside of the local network. These developments have led to the cloud architecture that now hosts the analytics, reliability, simulation and optimization tools operations teams need to stay competitive.
Conversely, OT has typically considered air-gapping the control system — ensuring its complete detachment from the internet and external systems — as a core cybersecurity measure. In reality, this point of view has never been entirely accurate. Few, if any, systems are entirely air-gapped, even if they are properly maintained. The perception of an isolated system is typically an illusion as the system will likely still be subject to cyber threats. Some form of data transfer device — whether a USB drive, engineering workstation or laptop — will need to be connected to the control system to keep it updated. These removable devices are potential vectors for intrusion, violating the air-gap concept.
Today, many OT teams are beginning to approach control system implementation and operation from a more IT-centric point of view. These teams recognize that targeted, secure cloud connectivity is possible, and needed to unlock capabilities like enterprise analytics for driving better performance, more sustainable operations and less waste across the organization. Meeting these needs means moving away from old ways of thinking, focusing instead on how to incorporate the control system as part of a connected automation infrastructure that leverages secure design to embrace the emerging IT/OT convergence, while providing extensive support to mitigate evolving cyber threats without process operations disruption.
Designed with security in mind
To meet the need for inherently secure automation platforms, automation manufacturers are developing new control technologies from the ground up with security in mind. But when it comes to cybersecurity, not all automation systems are created equal. The most advanced automation platforms will be built using secure-by-design development methods.
Secure-by-design automation software begins with a lead person certified in cybersecurity technologies driving the right practices across a development and testing team. The lead oversees coders and engineers, each of whom are also certified in secure development practices.
A secure-by-design strategy ensures that every line of code in the control system software is developed following cybersecurity best practices and contains the mitigations needed to address any observations highlighted by automated threat modelling tools. It also means review and validation of the project will be completed using best practice security strategies to score effectiveness, and to provide mitigation steps for solving any detected problems.
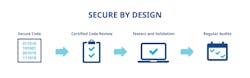
But cybersecure automation software development only begins with design and review, it does not end there. The best automation providers perform comprehensive testing with cybersecurity tools to ensure their software can withstand the threats they have been validated against. Designing systems that strive to comply with industry accepted standards such as the ISA/IEC 62443 series is a critical step, and regularly auditing those systems — with support from a third-party service provider if required — is essential to codifying that security (Figure 1).
Consider, for example, a web-based application that is part of the automation software, with the capability for connectivity to many different sources. The development team must first know they need to have filters in place to eliminate potential mishandling of scripts that might allow the application to connect to an untrusted site by mistake. But even with those filters in place, it is not until the software is tested live against known threats that it can be truly certified secure.
Partnering for success
Just as important as cybersecure design of automation software is the framing, organizing and execution of a company’s cybersecurity journey. In fact, the primary problem most plants beginning their cybersecurity journey face is that they “don’t know what they don’t know.” With thousands of available cybersecurity solutions designed to solve thousands of different problems, knowing where to start is often the most difficult step.
As IT and OT continue to converge in their strategies and goals, the IT department will be a critical partner in the development of a secure, connected automation platform. However, IT and OT still approach some critical standards — uptime, connectivity, standardization and more — very differently. Moreover, some plants simply do not have adequate IT support, making it hard to obtain clear guidance for projects.
Instead of relying solely on IT to help identify the right solutions — assuming there is an IT department with the time and resources to offer assistance — successful OT teams leverage their automation provider’s expertise to help close the remaining gap between IT and OT. If the team selected an automation solution with a clear history of cybersecure development, the automation provider should be able to help them successfully implement it. Expert automation suppliers are experienced and prepared to act as a liaison with IT to help ensure cybersecurity solutions meet the needs of both departments.
For example, selecting and developing the solutions that create a secure, connected automation platform requires extensive planning — typically via a front-end engineering and design (FEED) study. One of the first steps in that FEED study that will require collaboration between IT and OT is a gap analysis. As part of the gap analysis, the team will need to work closely with IT to define which cybersecurity baseline they will use as reference, so every stage can be measured against the starting point. It is much easier to judge and report success, and to gain support for later stages of the project, using this approach. An expert automation provider can help the OT team perform a gap analysis to identify its most critical needs, including the cybersecurity baseline for the entire automation platform.
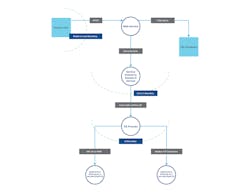
After identifying the baseline, IT and OT teams should work closely with the automation provider to help identify the cybersecurity technologies and policies they want to implement. Prioritization can be supported by a risk assessment, which needs to account for the impact to safety, production and environment. Finally, OT, IT and the automation supplier must align the execution plan to ensure efficiencies can be achieved during implementation, while always monitoring progress against the challenging moving target of industrial cybersecurity (Figure 2).
The value of continued support
Development of the modern secure automation platform does not end with installation and implementation of a solution. Cyber threats constantly change, so the automation platform must be ready to constantly evolve. To accomplish this, organizations must have a plan for lifecycle support to keep up with changing cybersecurity needs without disrupting operations.
As part of their refocus on cybersecure connectivity, forward-thinking automation solutions providers are developing comprehensive platforms to provide a wide variety of resources to help users navigate the ever-changing world of cybersecurity. They will also provide solutions to help teams keep their systems protected.
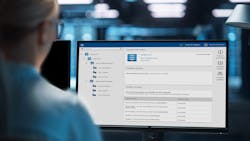
As an example, patching automation is one of many cybersecurity solutions an automation vendor might be able to provide. In this case, such solutions will not only identify new patches as they are released, but also identify which patches can be installed immediately, and which might need to be scheduled for later installation as they have a greater potential for disrupting system operation (Figure 3).
Ultimately, today’s OT teams should recognize that the journey does not end when cybersecurity systems are installed. They need to plan and partner to continually revisit and refine the solutions they have in place, while constantly improving the technology and the automation team’s cybersecurity maturity level.
Look for the leaders
The automation systems carrying process manufacturers into the future will not be locked away, with all their valuable data stranded. On the contrary, these systems will be highly-connected automation platforms, securely driving data across the enterprise to empower cross-functional teams to make better business decisions. OT teams need access to the analytics, simulation and reliability tools that will live in the cloud, but they will also need to be confident that access is secure, all the time.
Connectivity and cybersecurity go hand-in-hand, and the automation platforms that will bring your organization the most success with the least risk will be designed with this core principle in mind.
Claudio Fayad serves as vice president of technology of Emerson’s Process Systems and Solutions business. Prior to this role, Claudio held a variety of positions within Emerson, from sales and marketing director to vice president of software. He joined Emerson as director of Process Systems and Solutions in May of 2006, based in Brazil. Claudio holds a bachelor’s degree in engineering from the Universidade Estadual de Campinas and a master’s degree in business administration from Northwestern University.
Alexandre Peixoto is the cybersecurity business director for Emerson’s Process Systems and Solutions business. He has 20 years of experience in the process automation industry, and he has been with Emerson since 2010. Alexandre holds a bachelor’s degree of electrical engineering from the Universidade Federal de Itajubá and a master’s degree in business administration from Baylor University.
Emerson
About the Author
Claudio Fayad
Vice president of technology of Emerson’s Process Systems and Solutions business
Claudio Fayad serves as vice president of technology of Emerson’s Process Systems and Solutions business. Prior to this role, Claudio held a variety of positions within Emerson from sales and marketing director to vice president of software. He joined Emerson as director of Process Systems and Solutions in May of 2006 based in Brazil. Before Emerson, he started his career with Smar in 1995 as systems engineer and progressed through various roles of sales. Claudio served as the global engineering sales director in his last role with Smar. Claudio holds a bachelor’s degree in engineering from the Universidade Estadual de Campinas and a master’s degree in business administration from Northwestern University.
Alexandre Peixoto
Cybersecurity business director for Emerson’s Process Systems and Solutions business.
Alexandre Peixoto is the cybersecurity business director for Emerson’s Process Systems and Solutions business. He has 20 years of experience in the process automation industry, and he has been with Emerson since 2010. Alexandre holds a bachelor’s degree of electrical engineering from the Universidade Federal de Itajubá and a master’s degree in business administration from Baylor University.